Note
This feature is only available in the Professional release
Warning
This feature is only available on servers running the Apache web server. If your server is using IIS or NginX the button to launch this feature will not be shown. If you are using Lighttpd, Litespeed or any other server software you will see a button to launch this feature but this feature may not have any effect. If unsure please consult with your host about their server's support of .htaccess files.
One of the most important aspects of managing a web site hosted on an Apache server is being able to fine-tune your .htaccess file. This file is responsible for many web server level tweaks, such as enabling the use of permalinks, blocking access to system files which should not be accessible from the web, redirecting between pages based on custom criteria and even optimising the performance of your site. On the downside, learning how to tweak all those settings is akin to learning a foreign language. The tool of Admin Tools is designed to help you create such a file by utilizing a point-and-click interface.
Important
Some prepackaged server bundles and some live hosts do not allow using .htaccess files to override server settings. If it is a local server, edit your httpd.conf file and modify all AllowOverride lines to read:
AllowOverride All
If you are on a live host, please consult your host about the possibility of them allowing you to use this feature on your site.
Tip
If you ever want to revert to a "safe default", just set all of the options on this page to "Off" and click on "Save and create .htaccess". This will remove our custom code from your .htaccess file.
If you have manually edited the file and remove the special markers used by WordPress and / or Admin Tools to mark their sections of the file please delete the .htaccess file completely. Then go to Settings, Permalinks, choose another option and click on Save. Repeat that, this time selecting the option that was there before and click again on Save. If you are unsure please search "reset WordPress .htaccess" on your favorite search engine. There are hundreds of articles out there explaining how this works.
The bottom part of the .htaccess maker page contains the standard buttons you'd expect:
will save the changes you have made in this page's options without actually updating
the .htaccessfile. This should be used when you have not decided on some options yet.is the logical next step to the previous button. It not only saves the changes you made, but also updates your site's
.htaccessfile on the server. If you already had a.htaccessfile on your site, it will be saved as.htaccess.admintoolsbefore the file is updated, allowing you to go back to a safe state quickly.The button takes you back to the Control Panel page.
The rest of the page contains several panes with different options, described below. Before you change anything please read and understand the following warning. It is vital to not getting locked out of your site.
Warning
Depending on your web server settings, some of these options may be incompatible with your site. In this case you will get a blank page or an Internal Server Error 500 error page when trying to access any part of your site. If this happens, you have to replace the .htaccess file in your site's root directory using an FTP application or the File Manager feature of your hosting control panel. Remember that your old and working .htaccess file is saved as .htaccess.admintools before any changes are applied. You can rename that file back to .htaccess to revert to the last known good state. If you are unsure how this works, please consult your host before trying to create a new .htaccess file using this tool.
Some prepackaged server environments, like WAMPserver, do not enable Apache's mod_rewrite module by default, which will always result in an Internal Server Error upon applying the .htaccess file. Then again, these do not work with WordPress out of the box, unless you had completely removed the .htaccess file that ships with WordPress in the first place. If this is the case you are strongly suggested to enable mod_rewrite on your installation. On WAMPserver you can click on its tray icon, go to Apache, Modules and make sure rewrite_module is checked. On other server environments you have to edit your httpd.conf file and make sure that the LoadModule mod_rewrite line is not commented out (there is no hash sign in front of it). Once you do either of these changes, you must restart your server for the change to become effective.
We strongly suggest that you begin by setting all options to No and then enable them one by one, creating a new .htaccess file after you have enabled each one of them. If you bump into a blank or error page you will know that the last option you tried is incompatible with your host. In that case, remove the .htaccess file, set the option to No and continue with the next one. Unfortunately, there is no other way than trial and error to deduce which options may be incompatible with your server. This is exactly what we do on servers we have not set up ourselves.
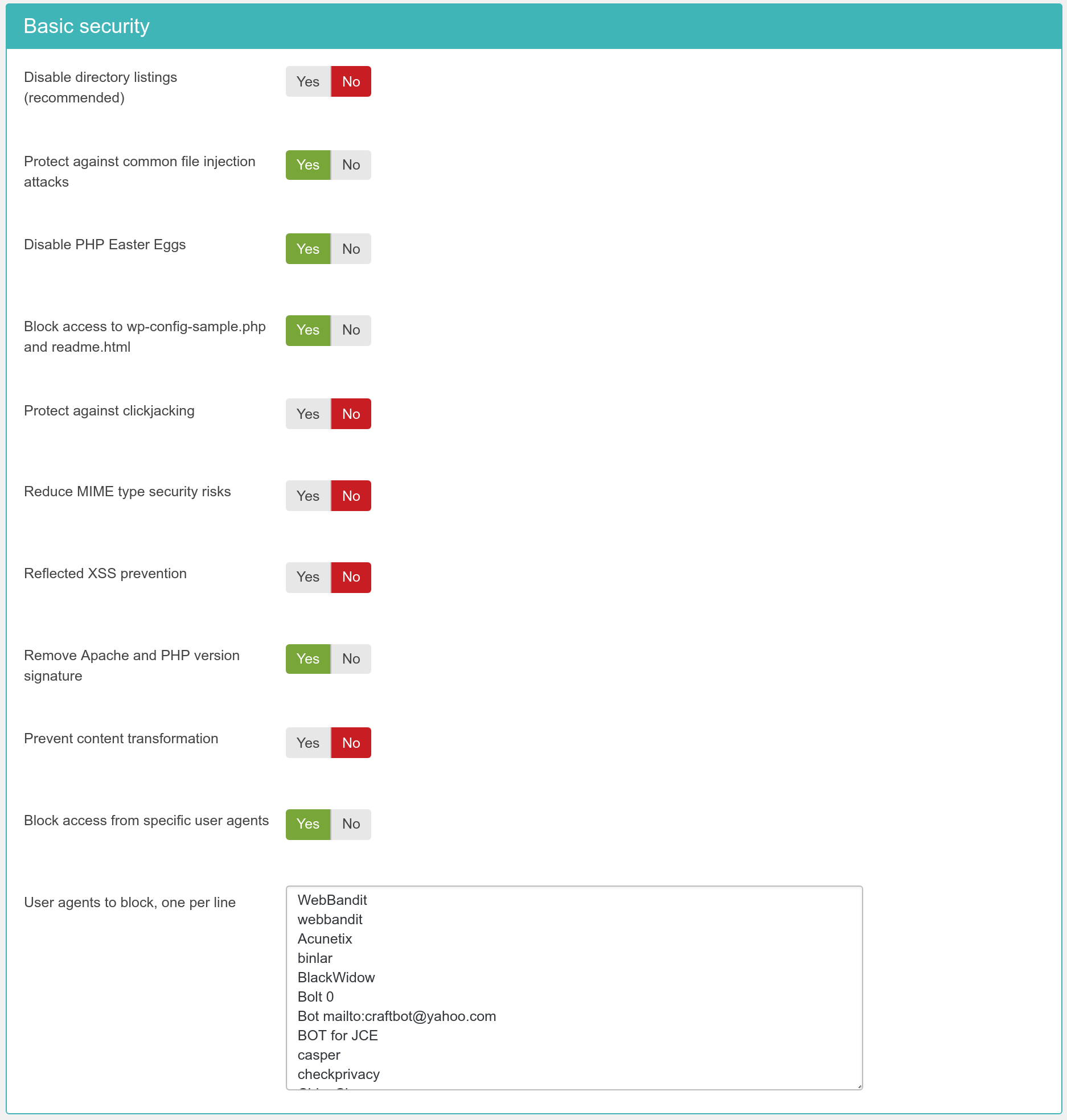 |
- Disable directory listings (recommended)
When disabled, your web server might list the files and subdirectories of any directory on your site if there is no index.html file inside it. This can pose a security risk, so you should always enable this option to avoid this from happening.
- Protect against common file injection attacks
Many attackers try to exploit vulnerable extensions on your site by tricking them into including malicious code hosted on the attacker's server. Enabling this option will protect your server against this kind of attacks. This works by preventing any URL which references an http:// or https:// URL in the query string. Sometimes these are legitimate requests. For example, some slideshow plugins use them. In this case you are recommended to use the RFIShield (Remote File Inclusion protection) in the Web Application Firewall and turn this .htaccess Maker option OFF.
- Disable PHP Easter Eggs
PHP has a fun and annoying feature known as "Easter Eggs". By passing a special URL parameter, PHP will display a picture instead of the actual page requested. Whereas this is considered fun, it is also widely exploited by attackers to figure out the version of your PHP installation (these images change between different versions of PHP) and launch hacking attacks targeting your specific PHP version. By enabling this option you completely disable access to those Easter Eggs and make it even more difficult for attackers to figure out the details of your server.
Note: You are advised to also set
expose_phptoOffin yourphp.inifile to prevent accidental leaks of your PHP version.- Block access to wp-config-sample.php readme.html
These two files are left behind after any WordPress installation or upgrade and can be directly accessed from the web. They are used by attackers to tell the WordPress version you are using, so that they can tailor an attack targeting your specific WordPress version. Enabling this option will "hide" those files when accessed from the web (a 404 Not Found page is returned), tricking attackers into believing that these files do not exist and making it slightly more difficult for them to deduce information about your site.
- Protect against clickjacking
Turning on this option will protect you against clickjacking. It does so by preventing your site's pages to be loaded in a, Frame, IFrame or Object tag unless this comes from a page inside your own site. Please note that if your site relies on its pages being accessible through frames / iframes displayed on other sites (NOT on your site displaying content from other sites, that's irrelevant!) then you should not enable this option. If unsure, enable it.
- Reduce MIME type security risks
Internet Explorer 9 and later, as well as Google Chrome, will try by default to guess the content type of downloaded documents regardless of what the MIME header sent by the server. Let's say a malicious user to upload an executable file, e.g. a .EXE file or a Chrome Extension, under an innocent file extension as .jpg (image file). When a victim tries downloading this file, IE and Chrome will try to guess the file type, identify it as an executable file and under certain circumstances executing it. This means that your site could be unwittingly used to serve malware. Such an event could result in your site being blacklisted by browser makers and cause their browsers to display a warning to users when visiting your site. By enabling this feature you instruct IE and Chrome to respect the file type sent by your server, eliminating this issue. See the relevant MSDN article for more information.
- Reflected XSS prevention
When enabled the browser will be instructed to prevent reflected XSS attacks. Reflected XSS attacks occur when the victim is manipulated into visiting a specially crafted URL which contains Javascript code in it. This URL leads to a vulnerable page which outputs this Javascript code verbatim in the page output ("reflects" the malicious code sent in the URL).
This is a commonly used method used by attackers to compromise web sites, especially when a zero-day XSS vulnerability is discovered in popular WordPress plugins or WordPress itself. The attacker will try to trick the administrators of websites into visiting a maliciously crafted link. If the victims are logged in to their site at that time the malicious JavaScript will execute, typically giving the attacker privileged information or opening a back door to compromising the site.
Enabling this option in .htaccess Maker will instruct the browser to try preventing this issue. Please note that this only works on compatible browsers (IE8; Chrome; Safari and other WebKit browsers) and only applies to reflected XSS attacks. Stored XSS attacks, where the malicious JavaScript is stored in the database, is NOT prevented. You should consider this protection a safety belt. Not wearing a safety belt in the event of an accident pretty much guarantees serious injury or death. Wearing a safety belt minimises the possibility of injury or death but does not always prevent it. This option is your safety belt against the most common type of XSS attacks. You should use it but don't expect it to stop everything thrown your way. Always keep your software up-to-date, especially when a security release is published!
For more information please consult the relevant MSDN article.
- Remove Apache and PHP version signature
By default Apache and PHP will output HTTP headers advertising their existence and their version numbers. If you are always using the latest and greatest versions this may not be a problem, but the chances are that your host is using an older version of both software. Giving away the version numbers of the server software in every request makes it trivial for an attacker to obtain information about your site which will help them to launch a tailored attack, targeting known security issues in the versions of Apache and PHP you're using. Enabling this option will mitigate this issue. Please note that this is SECURITY THROUGH OBSCURITY which is NEVER, EVER an adequate means of protection. It's just a speed bump in the way of an attacker, not a roadblock.
You are strongly advised to keep your server software up-to-date. If you're not managing your own server, e.g. you're using a shared host, we very strongly recommend choosing a hosting service which follows this rule. As a simple test, if your server is not currently using one of the PHP versions published in the top right corner of http://php.net (or at most one version earlier, i.e. the third number of the version on your server is one less than the one listed on php.net) the chances are that your server is using outdated, vulnerable server software. Remember that outdated versions of PHP and Apache, even with some security patches backported, CAN NOT be secure. There's a good reason new software versions are published regularly. For example a popular but woefully outdate version of PHP is PHP 5.3.3. It has a MAJOR issue regarding bcrypt encryption, fixed in 5.3.10 and NOT backported by any vendor to an earlier version of PHP. As a result using PHP 5.3.3 makes your site's passwords insecure.
- Prevent content transformation
Enabling this feature instructs proxy servers and caches to not convert your content. For example, certain proxy servers (typically found in mobile networks, businesses and ISPs in congested areas) will attempt to scale and aggressively compress images, CSS and Javascript to save bandwidth. This can lead to several issues, from displayed images being a bit off to your site breaking down because the compressed CSS/JS introduced errors preventing the browser from parsing it correctly. With this feature enabled the cache and proxy servers will be instructed to not do that by setting an HTTP header. If they respect the HTTP header (they should, it's a web standard) such issues are prevented.
For more information please consult the formal web standard document RFC 2616, section 14.9.5
- Block access from specific user agents
When enabled, it will block any site access attempt if the remote program sends one of the user agent strings in the User agents to block, one per line option. This feature is designed to protect your site against common bandwidth-hogging download bots and otherwise legitimate tools which are more usually used for hacking sites than their benign intended functionality.
- User agents to block, one per line
The user agent strings to block from accessing your site. You don't have to enter the whole UA string, just a part of it. The default setting includes several usual suspects. Separate multiple entries by a single newline character (that is a single press of the ENTER key). Do note that some server with mod_security or mod_evasive installed will throw an "Access forbidden" message if you try to save the configuration settings when this field contains the word "WGet". If you come across this issue it is not a bug with Admin Tools or WordPress, it is a server-level protection feature kicking in. Just avoid including the word Wget and you should be out of harm's way.
Default list of user agents to block
The following is the default list of user agents to block, as of Admin Tools 1.0.0.b1. It is very thorough and seems to be reducing the number of attacks enormously. If you are upgrading from an earlier version you might want to update the list manually (it's not updated automatically). Remember to enable the Block access from specific user agents to enable the feature and then click on to generate the .htaccess file which applies this setting on your site.
acapbot acoonbot acunetix ahrefs alexibot archiver asterias attackbot awario backdor base64_decode becomebot bin/bash binlar blackwidow blekkobot blex blowfish bolt 0 bot for jce bot mailto:[email protected] bullseye bunnys butterfly c99shell careerbot casper casper cazoodlebot checkpriv checkprivacy cheesebot cherrypick chinaclaw chinaclaw choppy clshttp clshttp cmsworld cmsworldmap comodo copernic copyrightcheck cosmos crescent custo datacha default browser 0 demon diavol diibot disco discobot disconnect dittospyder dotbot dotnetdotcom download demon dumbot ecatch econtext ecxi eirgrabber emailcollector emailsiphon emailwolf eolasbot eval eventures express webpictures extract extractorpro eyenetie feedfinder fhscan flaming flashget flicky foobot fuck g00g1e getright getweb! gigabot go!zilla go-ahead-got go-ahead-got-it gozilla grab grabnet grafula gt::www harvest heritrix hmview http::lite httrack httracks ia_archiver icarus6j id-search id-search.org idbot image stripper image sucker indy library interget internet ninja internetseer.com irlbot isc systems irc search 2.1 jakarta java jetbot jetcar jikespider joc web spider kmccrew larbin leechftp libweb libwww libwww-perl liebaofast linkscan linksmanager.com_bot linkwalker loader lwp-download lwp-trivial majestic mass downloader masscan maxthon$ mechanize mfc_tear_sample microsoft url control microsoft.url midown tool miner missigua locator mister pix mj12bot morfeus moveoverbot msfrontpage navroad nearsite net vampire netants netmechanic netspider netzip newt nicerspro nikto ninja nominet nutch octopus offline explorer offline navigator pagegrabber panscient.com papa foto pavuk pcbrowser pecl::http peoplepal petalbot phpcrawl phpshell planetwork pleasecrawl postrank proximic psbot purebot pycurl queryn queryseeker radian6 radiation realdownload reget remoteview rippers 0 rogerbot sbider scan scooter seamonkey$ seekerspid semalt siclab sindice sistrix sitebot sitecheck.internetseer.com sitecopier siteexplorer sitesnagger skygrid smartdownload snoopy sosospider spankbot spbot sqlmap stackrambler steeler stripper sucker superbot superhttp surfbot surftbot sux0r suzukacz suzuran takeout teleport teleport pro telesoft toata dragostea mea pentru diavola true_robots turingos turnit turnitinbot unserializ uri::fetch urllib vampire vikspider voideye web image collector web sucker webalta webauto webbandit webcollage webcopier webfetch webgo is webleacher webreaper websauger webshell website extractor website quester webstripper webvac webviewer webwhacker webzip wells search ii wep search wget widow winhttp woxbot www-mechanize wwwoffle xaldon xaldon webspider xxxyy yamanalab yioopbot youda zermelo zeus zmeu zune zyborg