 |
The Request Filtering section contains the options which are the heart and soul of the Web Application Firewall. Admin Tools will monitor incoming requests and their variables, filter them using these options and decide which requests seem to be nefarious, blocking them.
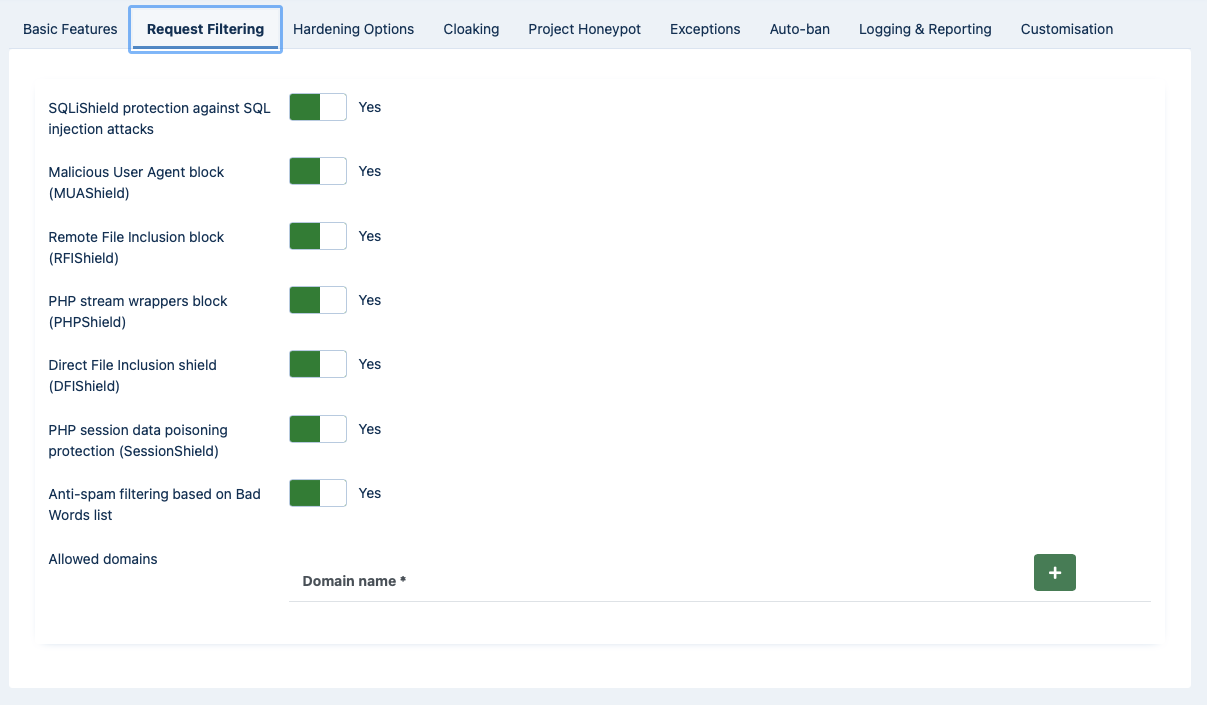
- SQLiShield protection against SQL injection attacks
When enabled, Admin Tools will try to detect common SQL injection attacks against your site and block them.
But what is a SQLi attack? A few Joomla extension developers are hobbyists, without experience and / or security training; or mistakes do happen, as Joomla itself has found out the hard way. One of the common mistakes they do is to make assumptions about the nature or the content of user-submitted data, interpolating them into database queries as-is. Database queries are also called SQL queries (SQL, pronounced "sequel", is the shorthand for Structured Query Language, the programming language the database queries are written in). An attacker can exploit this mistake by sending data which have the effect of terminating the developer's database query and starting a new one which either dumps privileged data -such as usernames and passwords- or modifies data into the database - such as adding a new Super User under the control of the attacker. This class of attacks is called an SQL Injection, or SQLi for short, since the attacker "injects" his own code into a SQL query running on the site.
- Malicious User Agent block (MUAShield)
Many hackers will try to access your site using a browser configured to send malicious PHP code in its user agent string (a small piece of text used to describe the browser to your server). The idea is that buggy log processing software will parse it and allow the hacker to gain control of your website. When enabled, this feature allows Admin Tools to detect such attacks and block the request.
- Remote File Inclusion block (RFIShield)
Some hackers will try to force a vulnerable extension into loading PHP code directly from their server. This is done by passing an http(s):// or ftp:// URL in their request, pointing to their malicious site. When this option is enabled, Admin Tools will look for such cases, try to fetch the remote URL and scan its contents. If it is found to contain PHP code, it will block the request.
Important
If your site starts throwing white pages when submitting a URL in your site's front-end, please disable this option. The white page means that your server is not susceptible to this kind of attack and doesn't properly advertise this to Admin Tools when requested. In this case, Admin Tools crashes while trying to scan the contents of the remote location, causing the white page error. Disabling this option in such a case poses no security risk.
- Remote PHP protocol block (PHPShield)
Some hackers will try to read the files of your site using the php:// wrapper and some advanced PHP filters. When this option is enabled, Admin Tools will block every request that contains the php:// string.
- Direct File Inclusion shield (DFIShield)
Some hackers try to trick vulnerable components into loading arbitrary files. Depending on the vulnerable component, the file will either be output verbatim or parsed as a PHP file. This allows attackers to disclose sensitive information about your site or run malicious code uploaded to your site through another vulnerable vector, e.g. an unfiltered upload of executable PHP code. When this option is enabled, Admin Tools will search the request parameters for anything which looks like a file path. If one is found, it will be scanned. If it is found to contain PHP code, the request will be rejected.
Important
This feature does NOT prevent dumping of non-PHP files, e.g. the
/etc/passwdfile of Linux servers.- PHP session data poisoning protection (SessionShield)
Prevents malicious input data which can be used to trick PHP's internal session handler into executing arbitrary code when it's restoring the user session.
The PHP session unserializer has a major bug which makes it misinterpret stored session data if they contain specific character combinations, overwriting the legitimate session data with the attacker-defined contents. Combined with some other features of PHP this can lead to the execution of arbitrary PHP code. In short, attackers can send malicious data in one page load and get arbitrary code to execute in the next page load. This feature of Admin Tools detects and blocks this kind of malicious data. CAUTION: It may block some legitimate requests as well.
Warning
This attack vector is NOT unique to Joomla!. It is a low level PHP bug / vulnerability which was fixed only in PHP 5.5.4 and later versions. Furthermore, default PHP settings even in newer versions of PHP use the old, vulnerable setting, putting all sites using session data at risk! We VERY STRONGLY recommend that all our clients use PHP 5.5.4 or later and edit their php.ini to modify this line:
session.serialize_handler = php
to
session.serialize_handler = php_serializeThis is the ONLY guaranteed way to fix this low level PHP vulnerability across all possible attack vectors, including those yet undiscovered.
- Anti-spam filtering based on Bad Words list
When enabled, all requests containing at least one word in the Bad Words list (configured separately, see the next sessions) will be blocked. By default the Bad Words list is empty; you have to configure it to match your site's needs. One good idea is to include pharmaceutical, luxury watches and shoes brand names, as this makes up the majority of comment and contact spam received on web sites.
- ItemidShield
Joomla's powerful frontend display comes, to a large extent, from being to configure its components and modules per menu item. Each menu item has a numeric ID, called “Itemid” in Joomla parlance. In fact, the Itemid is always present in the request parameters. When you have ‘Search Engine Friendly URLs’ turned off you can see it in the request. When it's enabled, Joomla automatically populates it from the URL query, i.e. the path in the URL you are using to access a page on your site (but in this case it can also be overridden in the URL). This is such a basic concept that Joomla's core code make the assumption that the Itemid is always a positive integer.
If someone makes a request with an Itemid which is not a positive integer, for example something like
https://www.example.com/foobar?Itemid=123/(note the slash after the number 123, it's part of the Itemid value!), Joomla will throw an error and a PHP exception email will be sent to you if you've configured this feature in Admin Tools. In most cases it's due to a search engine having cached an invalid URL like the one above. In some cases it might be a malicious probe with a technique called fuzzing, i.e. sending random data in known URL parameters to see if the site breaks in a way that can be exploited by an attacker. While Joomla itself will merely throw an exception, it is possible that system plugins executing before Joomla's router kicks in read the invalid Itemid and behave unexpectedly.The ItemidShield deals with these requests in one of the following ways:
Off. The ItemidShield feature is turned off. Any random Itemid value will reach Joomla and its extensions.
Clean. The ItemidShield will try to convert the Itemid value to a positive integer. If it fails, it will unset it, letting Joomla figure out the routing from the URL's path if any. This is the default setting with a balanced approach which offers security without risking blocking anything important.
Block. The ItemidShield feature will inspect the Itemid value. If it is NOT a positive integer it will block the request and record it as a Blocked Request in Admin Tools' log. Repeat blocked requests may get the IP address temporarily or permanently banned per your Auto-ban settings. This is a very defensive setting, recommended for sites being probed relentlessly.
- Block Suspicious Core Parameters
Joomla! has a number of query string parameters with a special meaning. These parameters cannot be used by extensions for any other purpose. Therefore, these parameters have a well-defined expected format. This feature checks whether these parameters follow this format. If not, the request is blocked.
Discrepancies between the expected format and the value in the HTTP request usually happen because of one of two reasons. The first reason is an attacker is trying to test your site for Reflected Cross-Site Scripting (Reflected XSS). In this case, the attacker tries to pass malicious JavaScript code, hoping that your template will output the malicious code verbatim in the output, making it executable. This can then be used to create maliciously crafted links which can lead to admins or users of your site getting hacked. The other reason is that there is a simple coding mistake in an extension, usually one which happens either under unexpected circumstances, or one which went by undetected because Joomla! “cleans” the content of core parameter query strings before using them. In the latter case, please contact the developer of the affected extension – NOT the developers of Admin Tools! – to address the problem in their code.
How this feature works
Admin Tools checks the value of the following query string parameters to ensure they are either unset, or their value follows the expected core Joomla! filter format for each one of them. This Admin Tools feature DOES NOT inspect the contents of each value, i.e. it does not try to make inferences about their meaning and validity, with the sole exception of the
typeparameter whenformat=feed(see below). The checks take place twice: in the onAfterInitialise and onAfterRoute events. The former runs as early as possible, checking the values coming into the application from the request (checking the $_REQUEST, $_GET, and $_POST PHP superglobals, as parsed by Joomla!). The latter checks the same values after Joomla! has performed SEF URL routing. Therefore, it makes sure that neither the request contains tainted data, nor that a rogue database entry or plugin corrupted the values of core variables.optionUsed to specify a component name. Admin Tools only checks that the format follows the CMD filter (see below), not whether the component exists.viewUsed to specify the view of a component. Admin Tools only checks that the format follows the CMD filter (see below), not whether the view exists.taskUsed to specify the task within a controller of a component. Admin Tools only checks that the format follows the CMD filter (see below), not whether the task is valid for the view / controller.controllerUsed to specify which controller in a component will handle the request. This is normally omitted, handled internally by the component. Admin Tools only checks that the format follows the CMD filter (see below), not whether the controller is valid for the component.layoutUsed to specify an alternative layout (view template) for the component's output. Admin Tools only checks that the format follows the CMD filter (see below), not whether the layout is valid for the component and view.tmplUsed to tell Joomla! which file in its current template (a.k.a. “system template”) will be used to render the page output. Usual values areindex(default, therefore normally omitted) andcomponent(just the component output, without any modules or other template chrome). Some extensions or templates use values adhering to the format but having no valid meaning in a template to trigger extension-specific behaviour. This option in Admin Tools only checks that the format follows the CMD filter (see below), not whether the tmpl value makes sense; for the latter, please see the Block tmpl=foo system template switch feature.templateUsed to tell Joomla! which template will be used to render the page output. Admin Tools only checks that the format follows the CMD filter (see below), not whether the template value makes sense; for the latter, please see the Block template=foo site template switch feature.formatUsed to tell Joomla! which rendered to use for producing its output. The default option ishtml, which generates HTML output. Other common options arexml,feed,json, andraw. When Joomla! does not know of a specific renderer under this name, it defaults toraw. For this reason, Admin Tools only checks that the format follows the CMD filter (see below), not whether there is a renderer matching the value of this parameter.langUsed to tell Joomla! which installed language will be used to render the page. Note that this is normally filled in by the language filter plugin, not passed as a query string parameter. Admin Tools only checks that the format follows the CMD filter (see below), not that the language referenced is installed; Joomla! will always fall back to the default language when you ask it to render a page in a language that is currently unavailable.ItemidUsed to tell Joomla! which menu item is the active one. This Admin Tools feature only checks whether the format follows the INT filter, not whether the menu item exists. For a more detailed approach to Itemid value filtering, please see the ItemidShield feature. When both feature are enabled, ItemidShield runs twice: before and after the Block Suspicious Core Parameters feature (technically speaking: in the onAfterInitialise and onAfterRoute Joomla! core events). This is intentional: the Itemid may not be set in the request, but retrieved from the database after Joomla! performs SEF URL routing.templateStyleUsed to tell Joomla! which template style will be used to render the page. It effectively overrides the template setting. Admin Tools only checks that the format follows the UINT filter (see below), not whether the template style value makes sense; for the latter, please see the Block template=foo site template switch feature.tpOnly applied when Preview Module Positions is enabled in the options page of Joomla's Templates component. This is used to tell Joomla! to display the module positions on the page to help developers identify the when deciding where to place a module. Admin Tools ensures that the value of this parameter when Preview Module Positions is enabled follows the INT filter.Note
The name of the parameter,
tp, stands for Template Preview, what this feature was implemented in Mambo, Joomla's predecessor.typeOnly applied whenformat=feed. In this case, thetypeparameter tells Joomla! whether to render the feed as RSS or Atom. Since the only three possible values in this case are unset / empty (defaults to RSS),rss, oratomAdmin Tools ensures that this parameter both follows the CMD filter format, and that its value is one of the three allowed ones.
The meaning of the filters listed above is exactly what Joomla! defines them to be, namely:
CMD: a single piece of text consisting of any combination of the unaccented Latin letters a-z, A-Z, numbers 0-9, and the special characters underscore, dot, and dash.
INT: An integer number, positive or negative.
UINT: A positive integer number.
- Allowed domains
This is a list of fully qualified domain names your site can be accessed on, one domain per line. DO NOT enter http:// or https:// in front, do NOT enter the / after the domain name or the path that follows it. This is a domain name, not a URL. For example:
example.com. You do not need to enter the www/non-www versions of the domain names or domain names which resolve to the localhost IP address (127.0.0.1 for IPv4 or ::1 for IPv6). If an attacker tries to access your site with an HTTP Host header that does not match these domain names (or their www/non-www versions) they will receive an HTTP 421 Misdirected Request error message.This feature mitigates a class of attacks called “HTTP Host spoofing” which affects a stark minority of servers, mostly servers which were set up by someone who doesn't understand web server security enough or at all. On those servers you can send an HTTP Host header which confuses the server into believing that this is the domain name it's running on. So, even though you are accessing a site on www.example.com you can send it a
Host: www.evil.hackHTTP header and now all URLs generated by the server will use the www.evil.hack domain name. This is used in phishing attacks to misdirect a submitted form with login credentials to a server under the attacker's control even though the browser's address bar shows a legitimate domain name.If you are on an affected server you are VERY STRONGLY recommended to use this feature INSTEAD OF setting the $live_site URL in configuration.php, the latter being the traditional but incorrect way of mitigating such an issue. Setting the $live_site URL limits your site to exactly one domain name (remember that example.com and www.example.com are two different domain names!) and protocol (HTTP vs HTTPS). Therefore using $live_site is extremely limiting and can cause your site to stop working if you try to enable/disable HTTPS everywhere in Joomla's Global Configuration, enable/disable www to non-www redirections etc. Moreover, the $live_site URL in configuration.php does NOT protect against all host spoofing attacks. What Admin Tools does will indeed protect all requests handled by Joomla against such attacks without causing any of the adverse effects of Joomla's recommended course of action.